Share this
The rise of Ransomware: Defending Against the Global Cyber Epidemic
by Tim Li, Technical Writer at Buffalo Americas on Dec 12, 2019 12:09:26 PM

With the meteoric rise of digital devices being used for global business applications in recent years, the number of cybercriminals has equally soared to prey upon victims with a wide range of cutting-edge malware. Among the different malware types, ransomware has been identified as one of the most prevalent and devastating, with no signs of slowing down.
According to a recent study by McAfee, the number of ransomware attacks has grown 118% in the first quarter of 2019, and new ransomware families have been identified utilizing innovative techniques to attack businesses.
At its core, ransomware is a type of malware that prevents you from accessing your files or system, essentially holding your data as "hostage" unless you pay a ransom. When a business is locked out of its devices or data, the effects can be extremely detrimental, ranging from lost profits due to immediate downtime to business collapse due to essential data loss. Ransomware has been responsible for some of the most high-profile cyberattacks in recent years.
Modern ransomware can target not only your computers but also your servers and mobile devices. From home users to small businesses, global corporations to municipal governments, no institution is safe from the threat of ransomware.
Buffalo recommends taking every measure in combining vigorous cyberattack prevention methods and robust, secure data backup solutions such as the TeraStation with multi-version backup and snapshot capabilities so that you can save yourself from the possibly catastrophic consequences of a ransomware attack.
Common Ransomware Types
Even though ransomware can take the form of many different families and variants, most of the time it tends to be one of two types: crypto and locker. Depending on which type of ransomware you encounter, knowing how it works may help you beat the threat.
Crypto
Crypto ransomware encrypts certain files and prevents you from accessing them until you pay the ransom, at which point the attacker promises to deliver a decryption key to unlock your files. Crypto ransomware has become the most prevalent type of ransomware, accounting for more than half of all ransomware attacks in 2017.
Due to the prevalence of digital data, victims who don't employ an effective backup strategy can be left desperate to retrieve their data, and default to paying the ransom rather than lose the data and suffer the consequences.
Crypto ransomware often isn't immediately noticeable when it first infects a system, as the malware doesn't go after critical system files or restrict functionality. Instead, the ransomware tends to focus on specific file types, depending on the target.
Crypto ransomware needs time to quietly locate and encrypt the files that could be valuable. By the time the ransomware announces itself, data has already been encrypted. With crypto ransomware, the user typically can still use the device as normal, apart from being unable to access the data that has been encrypted.
Locker
Locker ransomware locks you out of your devices, preventing you from using them until you pay the ransom. Locker ransomware typically manifests as a screen that locks out the device's user interface and leaves you with limited hardware capabilities, such as disabling your mouse and limiting your keyboard to only the numeric keys, so you can interact with the ransomware.
Since locker ransomware doesn't directly encrypt your files, it tends to be less damaging – and in some cases, easier to deal with. Locker ransomware can often be removed without too much trouble by data security software and services, which reduces the effectiveness of the ransomware itself in extracting payment.
Regardless of the type, ransomware is designed to prevent you from accessing your data. In this digital age, where data security is more important than ever, being caught unaware can have catastrophic consequences.
How Ransomware Spreads
Due to the myriad of ransomware families and strains, a big portion of protection against ransomware is knowing the landscape, so you'll know what you're up against. By becoming familiar with common ransomware intrusion and propagation methods, you can actively reduce your attack surfaces to protect your data.
Software and System Vulnerabilities
In data security terms, a vulnerability is an exploit that allows a threat actor to perform unauthorized actions within a system. Vulnerabilities can exist on any level of any data infrastructure, from the network hardware to the programs used to perform everyday tasks.
To exploit these vulnerabilities, threat actors often trick the victim into downloading an exploit kit (EK). An exploit kit is a software package designed to identify vulnerabilities in systems or applications, and serves as a platform to deliver various forms of malware using those vulnerabilities, including ransomware
Phishing Emails
Email spam is another common vector. Ever since email has become the ubiquitous and convenient communication method between digital users, attackers have learned to utilize email spam to spread malware, including ransomware.
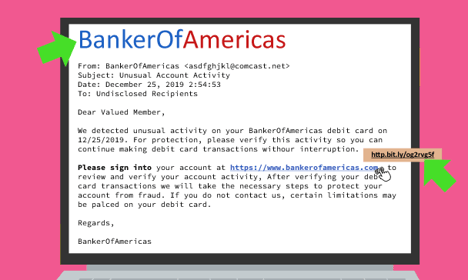
The spam usually comes in the form of an email containing an attached EK or ransomware in disguise, or a link in the email leading to a site hosting malware. Malicious emails are designed by use of social engineering and behavioral patterns, whereas fake email messages appear to be from friends or colleagues asking them to download a file, or the email can seemingly come from an established institution (such as a bank) or even resort to scare tactics, claiming to be from law enforcement and threatening legal action. Regardless, the result is the same: the user is tricked into downloading an email attachment or clicking a link, thereby resulting in a cyberattack with just a single click.
Malvertising
While exploit kits can be downloaded from nebulous sites, malvertising is another thing entirely. True to its name, malvertising is when a malicious advertisement is embedded within legitimate websites. When the advertisement is clicked, the user is directed to a site hosting an EK.
In the worst-case scenario, an ad containing an exploit kit is loaded and activated as soon as you visit a completely legitimate website. This is the most difficult aspect of malvertisements, as you may end up visiting a site that was safe in the past, but this time the website has been compromised, and you won’t have any idea.
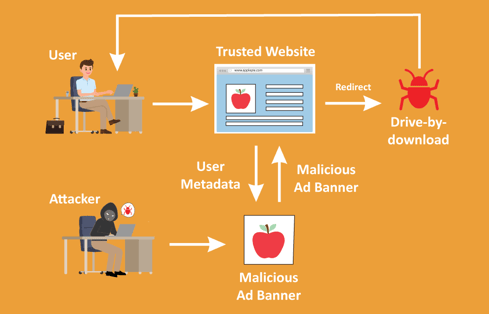
Cybercriminal groups often use a traffic distribution service (TDS) to redirect traffic to malicious websites based on filtered criteria such as time of day, geographic location, operating system, etc. Ad networks can be especially susceptible: when you click on an ad on a website, threat actors can use TDS to instead redirect you to a site hosting an EK, leading to what is commonly referred to as the “drive-by-download” of malware, where attackers make a user unwittingly download the ransomware itself.
Self-Propagation
Some ransomware variants are created with a built-in capability to spread. For example, Koler is a locker ransomware that attacks Android devices, but recently researchers have discovered a variant where it not only locks your Android phone, but also sends a spam SMS text to every person on your contact list with a URL that leads to the same ransomware. These ransomware worms are especially dangerous to enterprises as the infection of one device can quickly lead to other compromised devices on a network.
Ransomware-as-a-Service
Given the overabundance of attack vectors, data security experts have developed many strategies to counteract ransomware. As a result, underground cybercrime groups have been banding together to form affiliate systems to carry out widespread ransomware attacks.

Because of the enormously high success rate of ransomware attacks in netting payments, more and more underground cybercrime groups have developed products and services to be purchased by those who wish to deploy their ransomware attacks. In essence, they are providing ransomware-as-a-service (RaaS), and as a result, even relatively non-technical threat actors can carry out devastating cyberattacks.
As with any other business, RaaS groups have developed structured packages, roles, and even pricing models. For example, a group may only focus on developing and enhancing the ransomware, while another may specialize in effective propagation. By pooling their resources together in affiliate groups and splitting the profits, threat actors have more incentive than ever to launch ransomware attacks. The sheer convenience of RaaS has drastically lowered the barrier to entry into utilizing ransomware and is one of the many reasons why ransomware attacks are on the rise.
Ransomware Mitigation Strategies
While there is no bulletproof methodology for preventing ransomware, Buffalo recommends consolidating multiple prevention and preparation practices into a comprehensive, multi-layer data security strategy. Since every security layer would present an extra obstacle for attackers to overcome, you can help reduce the overall attack surface at various points in your enterprise’s data infrastructure.
Network Monitoring
Modern ransomware attacks can involve many different elements, and dedicated threat actors will not hesitate to launch multiple avenues of attack. One of the most important aspects of cybersecurity is robust network protection and monitoring. We recommend always staying aware of all traffic on your network. Common sense dictates that if you don't know what is happening on your network, attackers will be all too happy to exploit this.
But if you have a good picture of daily traffic, you can then take action to block unknown traffic and prevent exposing your system to risky sites and untrustworthy applications. Safeguarding your network with vigilant security is an active deterrent in and of itself. If you raise the cost of an attack for attackers, this reduces the likelihood of them pursuing a costly attack against you.
System security depends on your enterprise’s data infrastructure. You will need to inspect each endpoint and determine what security measures are needed for it. Ideally, each endpoint will have its protections set up as needed.
For example, corporate email systems should have content filtering and spam blocking, and corporate mobile devices should have messaging protection installed to block phishing messages and malicious URLs. You should also have password-based access protection and encryption to ensure safe data pathways. By blocking known attack vectors, you can remove these threats from the equation altogether.
Software Security
Antivirus software is indispensable for endpoint security as it can quickly catch unauthorized intrusions. With that said, modern antivirus software and regular scanning can only help you stay notified as soon as a foreign file is detected, as many of them won't be able to do anything once ransomware has taken hold. When considering antivirus solutions, research ones from trusted data security providers and their features.
For example, some software solutions offer anti-exploit technology that shields your system, browsers, and programs from noted vulnerabilities, thus adding another layer of defense.
As with any operating system or software, security vulnerabilities are typically patched at regular intervals to prevent attackers from exploiting them. Software companies such as Microsoft and Adobe regularly release security patches to address found vulnerabilities, but many users neglect to install these updates, thus opening up avenues of attack. Vulnerabilities can occur with any software, from your word processing program to even your web browsers, so always keep your software updated with the latest security patches to help prevent unwanted intrusions.
User Awareness
A fully developed security infrastructure is only as secure as its users, so it pays to be aware of any potential blind spots. User habits – both foundational data security practices and threat awareness – can go a long way in helping you address areas of vulnerability before they become problem areas. After all, what good is having a robust security infrastructure and backup process if users end up creating more attack surfaces?
You should take steps to prevent your users from inadvertently downloading malicious or otherwise compromised files. Some of these precautions are common sense, such as educating your users to never open any spam emails or messages from unknown senders, and never download any attachments or click on any links from suspicious emails. Along with patching software as mentioned above, you can also take steps to configure your web browser’s security and privacy settings to reduce its exposure. Delete any unused browser plugins, update the ones you use regularly, and consider installing an ad blocker to prevent intrusions from unknown or suspicious sources.
After you address your endpoint security, stay informed. User awareness plays no small role in data security. Stay abreast of new ransomware when they are discovered and learn how they work. Ransomware, like all malware, is constantly evolving, so it pays to know when malware deploys new zero-day exploits. Keeping aware of how attacks occur and spread can help you recognize and possibly avoid future attacks.
Backup
Always, always have a backup. Ransomware is constantly evolving, and even the latest anti-malware software may not be able to pick up on ransomware signatures. A recent global poll by data security firm Sophos identified that 77 percent of organizations were running up-to-date endpoint solutions at the time of a ransomware attack.
Even without the ever-looming threat of ransomware, backups should always figure into your enterprise’s business continuity and disaster recovery plans. With so much of our data no longer analog, having a backup plan isn’t just a good idea; it should be compulsory.

Many enterprises only utilize local backups, such as external hard drives or Windows utilities like VSS, but these options are simply not up to the task in combating modern malware. Some crypto-ransomware, such as the infamous Ryuk, will delete shadow copies and other local backups on the network. Cloud storage is an option, but that comes with its own set of issues, not least of all cost and less-than-ideal security.
A backup solution with strong encryption and kept isolated from your local computers is a paramount investment, as you can enjoy a secure backup location that you can access anytime to restore files should you need to. Buffalo recommends a secure NAS device isolated from the rest of the network to be used as your dedicated backup location. We also advocate the 3-2-1 plan: have three copies of your data on two different backup locations, with one copy stored off-site. We recommend looking into NovaBACKUP for Backup software, as PC & Server licenses do come with our network storage solutions.
Snapshots
In recent years, many enterprises have started using flat backup systems such as storage-level snapshots to complement their backup strategies. A snapshot essentially creates a copy of the system data at a given point in time. When needed, a snapshot allows you to simply revert data to the state at the time the snapshot was taken. In the event of a ransomware attack, instead of having to painstakingly convert the data from the backup source to a usable format, you can simply restore the data to a point in time just before the infection occurred, thus drastically lowering your recovery time objective (RTO) to mere minutes instead of hours or even days.
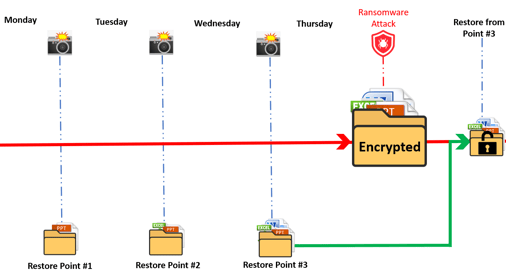
Snapshots go hand-in-hand with a secure, isolated backup solution as part of a multi-level backup strategy. Because snapshots are often stored at the same location as the original data, they are only as secure as your backup location. Also, not every storage solutions vendor offers devices with snapshot capabilities. When devising a detailed data security strategy, make sure the devices you choose will help you achieve your data protection goals.
Active Prevention and Active Preparation
As noted, there is no panacea against ransomware. In the face of such malicious ingenuity, the only real way to protect yourself is to make sure an attack does not happen. By combining active prevention (a detailed security plan) and active preparation (having a secure, isolated backup location for files), you can avoid being trapped in an unenviable position of having to perform a costly system restoration or negotiate with criminals
Dealing with Ransomware Attacks
If ransomware has already struck, stay calm. First and foremost, you will need to stop the malware from spreading. Isolate the infected device or devices and make sure they are kept off your network. Once you have contained the infection, you can then analyze the situation and consider your options.
Remove the Ransomware
Remove the ransomware from your devices so you can move forward and evaluate the damage. All things considered, ransomware is usually not difficult to remove, as you can typically delete it as you would any malware. The easiest way to remove ransomware (especially crypto-ransomware) is to put your computer or mobile device into Safe Mode, delete any temporary and infected files or apps, and then perform an antivirus scan to ensure that your system is free from the infection.
Reputable data security vendors such as Symantec and Norton provide tools to help users remove persistent malware. Removing the ransomware also helps you figure out what kind of ransomware you are dealing with and what your recourse is.

The issue with ransomware is dealing with the repercussions. For example, while crypto ransomware can be easy to remove, recovering encrypted files is nigh-impossible, which is why having a backup is so important, as you can still access your essential data. Once you have been attacked, unless you take immediate action, it is more than likely that you will be attacked again in the future.
Recover Your Data
If you have backups on hand, you should immediately restore the inaccessible data from the backup. If your system has been locked, you can perform a system restore after getting rid of the malware.
Buffalo recognizes that restoring from backups, especially entire systems, is neither simple nor convenient. A full restore can take time and system resources that you may not be able to spare, but they are essential in helping you avoid the risks of having to deal with criminals. This is where a secure backup solution, such as the TeraStation with multi-version backup and snapshot capabilities, can come to the rescue, as you maintain the flexibility to easily restore select files without hassle.
Contact Law Enforcement
If you are attacked by ransomware, you should contact law enforcement immediately. Even though you may feel that you can recover from a backup or otherwise recover your data, reporting your attack to law enforcement can help them develop a better understanding of how the attack works, and possibly contribute relevant information towards other ongoing ransomware cases and stay up-to-date on new attack types on the horizon. Any information may help law enforcement determine who is behind the attack, and your best recourse.
To Pay or Not to Pay
If you do not have a robust backup or other tenable options, you may end up wondering: "Should I just pay?".
While many advocate against paying, no matter what the consequences, we recognize that it is often not a black-and-white issue. Sometimes, serious logistical issues come into play. For example, you may not have the luxury (or even resources) to initiate a full system restore. This is a primary reason threat actors prefer to attack home users, SMB enterprises, and public offices: because they are often working with limited resources that inhibit their options. Restoring backup files can be a costly and time-consuming endeavor.
When you factor in the costs of performing a full restore and the money lost while your business experiences downtime, the overall cost may end up seriously crippling your business when compared to the cost of simply paying the ransom. In fact, according to a study done by IBM, over 70% of companies attacked in 2016 have paid the ransom, and over half of the users said that they'd be willing to pay to recover data rather than risk losing it.
Of course, there is certainly merit in not paying the ransom. Giving in to the attackers' demands serves only to further encourage and fund more attacks, not to mention the very sobering fact that even if you pay the ransom, there is no guarantee that you will get your data back. There have been countless instances of ransomware victims paying the ransom, only to receive a decryption key that doesn't work or simply no response at all. In addition, paying the ransom might subject you to consequences that may not be immediately obvious.
Security experts agree that victims who pay have a higher chance of being targeted again in the future, as attackers are likely to label the victim as a “soft target” who demonstrates a willingness to pay. And of course, there is the personal protection factor: when conducting financial transactions with criminals, the risk of identity theft is very real. Simply paying to get your data back is never a risk-free option.
While your initial instinct may be "No way am I paying!", some modern security experts advise keeping paying the ransom a valid option when considering all options. Even the FBI, in their publication on ransomware prevention and response, clearly advocates not paying but also recognizes that an enterprise victim should perform a detailed cost-benefit analysis on whether to pay when attacked. The data demonstrates that this is simply not a cut-and-dry decision. If a ransomware attack occurs, only you can decide what is the best option for you.
No Silver Bullet for Ransomware, but Not Hopeless Either
In recent years, the rise of ransomware has become a significant data security threat to both home users and businesses alike. With the advent of sophisticated and effective data security solutions, ransomware has likewise evolved to become even more sophisticated and effective.
To prevent putting yourself into the position where you're forced to make a Hobson's choice, consider taking steps to prevent the ransomware attack from happening. If a ransomware attack occurs but you can quickly isolate the infection and restore your data without much trouble, you stand a very good chance of recovering from the attack with a little worse for wear. Practicing safe computing habits and deploying a multi-layer data security plan along with a secure, isolated backup location can go a long way in helping you combat ransomware.
Share this
- Pre-Sales Questions (91)
- Tips and Tricks (89)
- Industry News (37)
- Best Practices (35)
- Reseller / MSP (31)
- Security Threats / Ransomware (26)
- Disaster Recovery (24)
- Cloud Backup (22)
- Storage Technology (22)
- Compliance / HIPAA (20)
- Applications (18)
- Backup Videos (15)
- Virtual Environments (12)
- Technology Updates / Releases (7)
- Backup preparation (5)
- Infographics (5)
- Products (US) (4)
- Company (US) (1)
- Events (1)
- Events (US) (1)
- Unternehmen (1)
- December 2025 (1)
- November 2025 (1)
- October 2025 (2)
- September 2025 (1)
- August 2025 (1)
- July 2025 (1)
- June 2025 (2)
- May 2025 (2)
- April 2025 (2)
- March 2025 (1)
- February 2025 (2)
- January 2025 (2)
- December 2024 (1)
- November 2024 (2)
- October 2024 (1)
- September 2024 (2)
- August 2024 (1)
- July 2024 (2)
- June 2024 (3)
- May 2024 (1)
- April 2024 (2)
- March 2024 (3)
- February 2024 (2)
- January 2024 (1)
- December 2023 (1)
- November 2023 (1)
- October 2023 (1)
- September 2023 (1)
- August 2023 (1)
- July 2023 (1)
- May 2023 (1)
- March 2023 (3)
- February 2023 (2)
- January 2023 (1)
- December 2022 (1)
- November 2022 (2)
- October 2022 (2)
- September 2022 (1)
- July 2022 (1)
- June 2022 (1)
- April 2022 (1)
- March 2022 (2)
- February 2022 (1)
- January 2022 (1)
- December 2021 (1)
- September 2021 (1)
- August 2021 (1)
- July 2021 (1)
- June 2021 (1)
- May 2021 (2)
- April 2021 (1)
- March 2021 (1)
- February 2021 (1)
- January 2021 (1)
- December 2020 (1)
- November 2020 (1)
- October 2020 (1)
- September 2020 (3)
- August 2020 (2)
- July 2020 (1)
- June 2020 (1)
- May 2020 (1)
- April 2020 (1)
- March 2020 (2)
- February 2020 (2)
- January 2020 (2)
- December 2019 (1)
- November 2019 (1)
- October 2019 (1)
- August 2019 (1)
- July 2019 (1)
- June 2019 (1)
- April 2019 (1)
- January 2019 (1)
- September 2018 (1)
- August 2018 (3)
- July 2018 (2)
- June 2018 (2)
- April 2018 (2)
- March 2018 (1)
- February 2018 (1)
- January 2018 (2)
- December 2017 (1)
- September 2017 (1)
- May 2017 (2)
- April 2017 (4)
- March 2017 (4)
- February 2017 (1)
- January 2017 (1)
- December 2016 (1)
- October 2016 (2)
- August 2016 (3)
- July 2016 (1)
- June 2016 (2)
- May 2016 (6)
- April 2016 (5)
- February 2016 (1)
- January 2016 (7)
- December 2015 (6)
- November 2015 (2)
- October 2015 (5)
- September 2015 (1)
- July 2015 (1)
- June 2015 (2)
- May 2015 (1)
- April 2015 (3)
- March 2015 (3)
- February 2015 (3)
- October 2014 (2)
- September 2014 (6)
- August 2014 (4)
- July 2014 (4)
- June 2014 (3)
- May 2014 (2)
- April 2014 (3)
- March 2014 (4)
- February 2014 (5)
- January 2014 (5)
- December 2013 (4)
- October 2013 (6)
- September 2013 (1)

